The interplay of CE-IoT as an enabler for green innovation and e-waste management in ICT
Abstract-The growth of the global middle class provokes significant increment in product consumption. As the available resources are limited, Circular Economy (CE) raises as a promising initiative towards the sustainable development. Except from the traditional approaches of reusing or recycling products, the current trend utilizes modern computer technologies and involves a data-driven aspect. The Internet of Things (IoT) is the main enabler for the integration of CE with technology. This paper proposes a framework for implementing the cooperative vision of CE and IoT. Via this solution, a pilot system is developed in a medium size telecommunication company for administrating the lifecycle of the deployed electronic equipment and the management of the related supply chains. Mechanisms and devices are maintained/repaired/fabricated in a regular basis, green computing techniques are efficiently applied, and the productive period is prolonged. When the business upgrades the system, the retired counterparts can be sold in start-ups or gifted in third-world countries. The overall approach extends the working period of the well-maintained electronic assets not only for the examined business but for the collaborating organizations as well. Recycling companies can then trace this supply chain and the assets’ status in order to define their investment strategy at the end-consumer, contributing in the reduction of the electronic waste problem in the third-world.
Keywords—Circular Economy; Internet of Things; Sustainable development; Green computing; E-waste; Circularity by Design; IoT; IIoT;
I. INTRODUCTION
The continuous raise of the world population and the expansion of the global economy are stressing the planet’s physical resources. As the environmental sustainability is threatened, several governmental initiatives try to tackle the problem. Green innovation is gaining ground the last years due to the environmental movement and climate change (e.g. [1], [2]). In 1997, United Nations adopted the Kyoto protocol to reduce the greenhouse gases emissions and counter global warming. The main period of the protocol expired in 2012 and its extension until 2020 was announced. Circular Economy (CE) is such an act towards a regenerative system, where the consumption of new resources is minimized by extending the lifecycle of current products ([3], [4]). The economy is formed in closed loops and the materials are reused over-and-over by the various actuators. The main states of a CE model include long-lasting design, maintenance, repair, reuse, remanufacturing, refurbishing, and recycling. The adoption of the CE principles in a large scale inevitably leads to economic transformation and the establishment of new business models [5]. An ambitious innovation package by the European Union (EU) is provoking this evolution in the Old World [6] and the global economy. Significant efforts are also devoted by the Chinese government [7]. Except from the ordinary CE settings, the integration with Internet of Things (IoT) technologies is now emerging [8], [9]. Pioneer services for smart city and intelligent transportation are popular here, while other significant economic sectors, like the Information and Communications Technology (ICT), have not gain much attention. This paper proposes the CE-IoT: a data-driven framework that materialize the CE business model and the integration with the IoT infrastructure. An organization observes the deployed equipment status via system monitors and IoT devices that gather related knowledge. The information is then collected and processed by machine learning (ML) and data-analytics algorithms. The results are parsed to decision support systems (DSS) that outcome the organization’s administration strategy. The reactive policy is implemented by artificially intelligent agents that manage the system at runtime and facilitate the CE actions. Green computing techniques can be also enforced increasing the utility of the current products [10]. The presented solution is quite generic and applicable in various CE-IoT settings. Nevertheless, we demonstrate its deployment in ICT organizations. Thus, a preliminary version is developed and the main functionality is tested under the cloud infrastructure of the medium-scale ICT provider, Cablenet, with collaborating organizations being emulated. To our knowledge, this is the first concrete implementation of the interplay between the CE and IoT visions in the ICT domain.
The rest of the paper is organized as: Section 2 mentions the related work in the field of CE and IoT. Section 3 sketches the CE-IoT framework and the deployment on the ICT organization. Sections 4 presents the machine learning and data analytics procedures that enhance forecasting and the establishment of green computing policies. Section 5 details the decision making model and the administration of the CE actions. Finally, Section 6 concludes and refers future work.
II. RELATED WORK
A. CE and IoT
CE review studies in [3] and [4] present the business principles of the new initiative. Further CE models and indicative examples are detailed in [5]. Smart devices and the IoT ecosystem enable new forms of interaction and business models. The transformation of the traditional market into a service-oriented setting is now a fact. The integration of CE and IoT further promotes such data-driven service-oriented
architectures (SoA) [8], [9]. Related cases are presented below, deriving the various examples from innovative industrial sectors.
The tire company Michelin added Fleet Solutions [11], a leasing application for EU trucking fleets, manner back in 2000. The business-to-business enterprise initiative leases “tire services” per the kilometer, charging a flat fee that scales primarily based on automobile type and distance pushed. The organization states that the carrier reduces the risk of fluctuating costs that include variability in tire performance, purchase fees, and unpredictable damage costs from owning the tires. Rather than requiring clients to pay prematurely for the tire and fee of changing it, Michelin absorbs a number of that risk.
Cars are from several perspectives one of the most beneathutilized sources in modern lifestyles. A research in Denmark reveals that an average vehicle transports around 1.4 humans on the street and spends about 23 hours per day taking up parking space [12]. Empty automobile seats are the most
important excess ability within the shipping enterprise, and this inefficiency has a poor impact at the environment and is highly-priced for car proprietors. GoMore’s platform [13] offers a provider that permits drivers to ask persons to join a journey on an already planned course. This will increase the quantity of people in vehicles and reduces the range of cars on the streets, making automobile journeys greener and friendlier for the environment. It results a travel solution that is inexpensive for both the auto owner and the passenger. Given that GoMore changed into mounted in 2005, more than 1 million users have visited and used the service. As an end result, more than 300,000 seats have been bought only in Denmark, making GoMore a European chief in combining ridesharing and peer-to-peer vehicle condo, and Scandinavia’s
main commercial enterprise inside the sharing economy.
In 2014, the French train manufacturer Alstom commenced imparting HealthHub [14], a predictive protection device that monitors the health of trains, train infrastructure, and signaling structures. It uses advanced information analytics to extend and maintain the beneficial life of trains. HealthHub uses records to capture and diagnose the degree of performance of wheels, brake pads, and put on-and-tear-inclined pantograph carbon strips (the framework that conveys currents to trains from overhead wires). The German organization MAN Truck & Bus is a main international provider of commercial and transport vehicles to companies. It offers support and advice with car design for fleets, operations, infrastructure, carrier, and maintenance. Last year, MAN rolled out a data-driven service to assist commercial truck and bus fleets with the transition to low carbon transportation [15]. Specifically, the corporation is that specialize in helping companies with challenges which includes variety making plans, charging infrastructure and battery swapping issues, capacity planning and loading times, and considerations round heating and air-conditioning requirements.
B. Green ICT
On the other hand, ICT is one of the main contributors of the financial system. The ICT infrastructure consumes the 3% of the global energy and produces about 2% of the global CO2 emissions [16]. The trend of green computing and networking includes practices of selecting energy efficient computing technologies and products, minimizing resource consumption whenever possible [2]. The Climate Group and the Global eSustainability Initiative estimated that such movements could reduce the global emissions by 15%, achieving around an eight-fold benefit comparing to carbon reduction expectations [17].
In general, the green ICT paradigms try to reduce the consumption of non-renewable resources (e.g. [7], [18], [19], [20], [21]). The integration of the two domains [22], [23] tries to provide efficiency along the supply chain for the involved products [24], [25], offering better rental [26] and e-waste services [27], [28]. New business models are then applicable materializing the so called recycle-rewarding system (RRS), like the e-waste management framework in [29]. In the current ICT setting, a typical business would use the bought equipment and serve the customers’ operations. When a damage occurs, the counterpart is either repaired or replaced by a new one. The retired equipment is threw away or recycled. If the company participates in a collaborative movement, the machinery could be re-sold in a low price or gifted to an organization in a third-world country. Such actions have led to an important increase of the Internet users and the expansion of the ICT sector in these countries [27]. On the other hand, the problem of environmental pollution and electronic waste (Ewaste) has emerged. As these end-users do not have the adequate capacity to repair occurring breakdowns of the outdated equipment, it becomes useless and ends up in stockpiles, landfills, or swamps [28]. The CE-IoT framework integrates the two sectors of CE and IoT. The efficiency of this combinatory approach is tested on the ICT industry. The case study that is presented in this paper, details the appliance of the proposed setting on Cablenet. Cablenet is a privately-owned company in Cyprus that offers telecommunication and entertainment services to the retail and corporate markets. The network capacity is terminated in key European locations and operates a fully redundant, self-healing ring in mainland Europe over multi10G capacity. Among the various Cablenet’s products and services, CE-IoT is deployed and administrates a cloud services platform that is offered to the end-customers. With CE-IoT in place 6 main goals are accomplished:
- The current host organization monitors the assets status and maintains them regularly and proactively, avoiding breakdowns and economic loss
- Green computing is applied by promoting policies that distribute the computational/communicational effort among inactive intervals, limiting the equipment overworking during peak periods
- The damaged products are repaired or fabricated and they are reused, extending their beneficial lifecycle
- When the company performs a system upgrade, the retired equipment is sold to startups or gifted in thirdworld countries, contributing to the collaborative acts
- If the equipment cannot be fixed, it is recycled, reusing the available materials in order to manufacture new products
- The recycling organizations can gather information from the involved parties in order to facilitate their investment strategies closer to the end-consumer, improving their operation
III. CE-IOT FRAMEWORK
In this subsection, we present a preliminary implementation of the CE-IoT framework on real devices and the deployment
on the cloud platform. The system is also applied in an emulated supply chain of the telecommunication sector where data are collected in real-time by IoT technologies and decisions are taken automatically regarding the CE aspects of the system’s maintenance and equipment supply.
A. The Cloud Services Platform
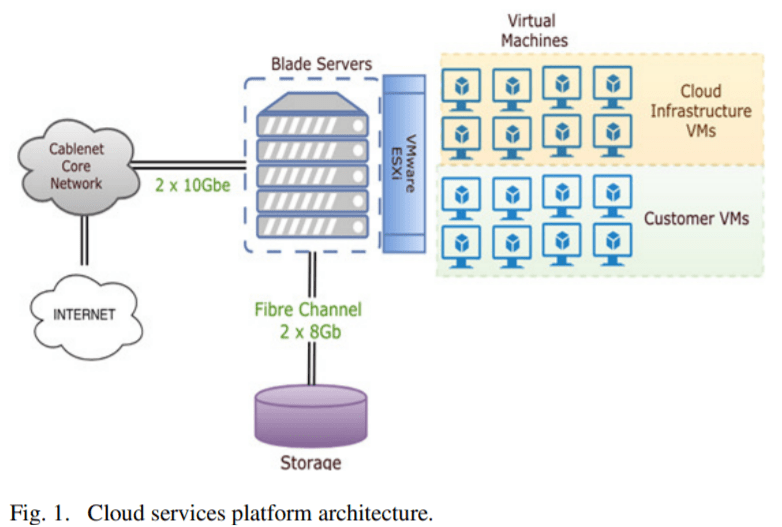
The evaluated cloud services platform is hosted on Cablenet’s infrastructure and the provided services include: i) hosted exchange email, ii) web hosting with personalized cloud control panel, iii) cloud server and mini Virtual Private Server (VPS), iv) cloud backup with support on workstations, servers,
and Virtual Machines (VMs), and v) Domain Name System (DNS) hosting. The high-level architecture of Cablenet Cloud Platform includes different parts as depicted in Fig. 1. More precisely, the most significant parts compiling the platform infrastructure and functionalities are listed below:
- Cloud platform is deployed utilizing Cablenet’s Datacenter Virtual Infrastructure (DVI). DVI is physically protected by a number of protection measures focusing on controlling physical access, mitigating power‐related risks, providing air conditioning and fire suppression
- One of the major roles on the provision of DVI is the heavy-duty support by the Internet Protocol (IP) / Network infrastructure, which is the backbone towards providing high quality connectivity and resiliency for the DVI cloud services
- Backbone/Core network operates based on multi-10G self-healing and fully meshed setup and provide connectivity over IP Multiprotocol Label Switching (MPLS) / Virtual Private Network (VPN) throughout all points of Cablenet presence and beyond
- Data access is provided via multi-10G redundant connections towards the cloud blade center depending on the data exchange traffic and needs, as well as in similar manner storage is directly connected on the cloud blade chassis for the storage/inventory
- The DVI includes installations of several products and components to provide its services and ensure their security from an IT perspective, including Microsoft’s Exchange server and tools for clustering and replication such as the VMWare High Availability Cluster, Microsoft Cluster Service on VMware vSphere and VMware vSphere Replication
- DVI’s set up includes also tools for security, anti‐malware management, data encryption and secure communications, as well as tools for managing the quality and Security and privacy requirements operation of the data center infrastructure (e.g., tools for executing backup processes, identifying improvements to server application or maintenance levels, adjusting parameters and physical resources such as memory, CPU, disk).
B. IoT Technologies
A popular choice for materializing an intelligent application is the agent technologies (e.g. [30], [31], and [32]). Software agents collect ambient information from the underlying subsystems and manage them based on artificially intelligent procedures. The most commonly utilized and supported enabler is the Java Agent DEvelopment platform (JADE) [33].
For the semantic representation of the knowledge and reasoning concepts, we select the Discrete Event Calculus Knowledge Theory (DECKT) – an implementation of Event Calculus (EC) in the rule engine Jess [34]. Reasoning is formed as an agent’s behavior and is embodied in JADE agents.
The various agents can also exchange knowledge. The FIPA standardized Agent Communication Language (ACL) [35] is selected for this purpose. The agents communicate wellformed messages based on the ACL format containing events, alarms, or other reports and notifications for the evaluated system.
- CE Decision Making
In the telecom CE-IoT scenario, we deploy JADE agents for administrating distinct subsystems of the examined organization (the abovementioned cloud services platform components). The agents receive messages from their underlying IoT devices and process them based on the DECKT-enabled reasoning process. These local agents are close to the edge system and perform the required embedded intelligence.
For this demonstration setting, the smart agents model the Location, Condition, and Availability (LCA) perspectives of the system. The agents are aware for each component’s location, its working condition, and the availability. More specifically, the three properties are determined as:
- Location: the physical location of the component (i.e. the room where a server is installed)
- Condition: good or requiring maintenance, repair, refurbishment, and recycling
- Availability: working, ready for reuse, or broken
Once entered in the organization, the component’s location is recorded by the system operator. Initially, it is of good operational condition and is either placed and working immediately or waits to be used. Nevertheless, when a component is integrated in the system and performs the desirable functionality, the operator determines the maintenance strategy. Three maintenance types are defined as:
- Periodic: implemented as a triggered event in the accountable agent’s reasoning behavior after a specified period (e.g. every three months)
- Decay: the agent collects usage data for the component and raises a maintenance event when it exceeds a threshold (e.g. after 1000 hours of operation)
- Or a combination of the two.
Meanwhile, if the component is broken, the operator specifies the new condition as requiring repair/refurbishment/recycling and the maintenance events are postponed. If the component is
repaired, the good operational condition is restored and the component is available for reuse.
The local agents also exchange this information to similar agents that are placed in the upper system layers and the backend infrastructure that implement the high level business intelligence. This includes, among others, the presentation of integrated reports to the high level management or even the automated communication with the relevant agents from cooperated businesses and the planning of adequate and timely equipment supplies.
Except from the LCA properties, the agents also gather the data for the ML algorithms that enable the green computing features. The ML procedures and detailed in the next section.
D. Scalability and Performance
As concerns the scalability and performance of the agent artificial intelligence and reasoning, Jess implements an efficient pattern matching method. The computational complexity is linear to the working memory size, and more specifically, it is strongly affected by the number of facts that are required in order to model the components of the underlying subsystem. In the examined scenario, each component requires around 10-20 facts to be modelled, resulting only in a low processing overhead in the nanosecond range. Fig. 2 depicts the agent GUI, 4 emulated components and the triggered event where the component C1 needs maintenance.
We demonstrate the proposed CE-IoT framework in anemulated environment, where BeagleBone embedded devices imitate the operation and the LCA properties of the organization’s components. Totally, we deploy 4 devices that communicate information to the relevant agent that runs on a local computer. On average, it takes 57 ms to perform a reasoning operation, requiring 40 MB RAM and 1.8 MB code
size.
IV. GREEN COMPUTING & EDGE INTELLIGENCE
In this subsection, we further extend the main monitoring framework with machine learning (ML) techniques (e.g. [36], [37]). Lightweight ML algorithms at the edge process the collected data from the local agents. Then, predictions are made concerning the maintenance of the monitored assets. Data analytics are also performed at the backend with mainstream ML technologies enhancing the overall business logic and the applied CE strategies.
A. Smart sensing and prediction
Smart monitoring/prediction is heavily based on the AI embedded sensing platform used in the field (layer) to sense the physical world, obtain the raw signals and thus, collecting the data in a parallel fashion. These units also include self-learning, self-adaptive, self-configuration, and selfmanagement capabilities. The platform utilizes a sophisticated design methodology imposing a hierarchical, naturally distributed, thus scalable, processing chain.
Towards this twofold direction (of monitoring and prediction), the set of AI sensing units can be placed in the specific locations of the ICT infrastructure measuring a wide range of qualitative characteristics such as traffic load, CPU usage, memory consumption, room temperature or humidity etc. The robustness of the ICT network can be reflected in the aforementioned parameters. Dependability could be compromised by equipment aging, overworking, sudden environmental conditions, etc. Those threats can lead to failures resulting in significant economic losses.
The critical infrastructure is monitored through the AI embedded sensing platform. The collected data are processed locally and then transmitted to the upper IoT architecture level, which includes a data center capable of further analyzing the acquired information.
During monitoring, raw/physical data are collected and processed (by each sensing unit) in a real-time fashion. It should be highlighted that monitoring is strongly related with event detection and thus, online machine learning algorithms can be applied in order to identify specific abnormal patterns
within the streaming data. Moreover, feature extraction and feature selection can be applied in each sensing unit (in a distributed manner) to reveal the hidden inter-sensor data information structure. The estimated features could then be transmitted to the backend for further processing, i.e., performing event detection. Several off-the-shelf approaches could be adopted for event or anomaly detection such as Hidden Markov Models (HMMs), autoencoders, Long Short Term Memory (LSTM) autoencoders, k-NN (nearest neighbor), and Local Outlier Factor (LOF) ([38], [39]). Moreover, data fusion-based event detection algorithms could be devised to achieve higher detection rates by exploiting multisensory data fusion.
As aforementioned, the analyzed data are sent to the backend for prediction purposes. The aggregated data can be exploited for long-term prediction towards identifying specific time of failures, estimating the parts of the infrastructure that are about to malfunction and in general ensuring that potential problems are discovered well before they actually occur. Prediction of critical events can be performed using decision trees, support vector machines (SVMs), deep learning and other machine learning time-series forecasting/prediction techniques ([38], [39]).
It is obvious from the description above that monitoring is taking place at the edge of the IoT system related with online, real-time detection, while prediction is related to short or long-term estimation of critical events. The extracted special data transferred from the lower edge level to the upper cloud/data center level can be used for prediction. However, continuous data aggregation can be exploited to retrain the predictor and an updated version of the monitoring algorithm can be obtained by sending down data that are computed during the prediction procedure. As a result, this information from the upper level can be used to obtain an updated robust monitoring version at the edge level, since we can determine what type of sensed data is needed to be acted on quickly and what can be analyzed at a later time. In some cases, it may be determined that certain data points are not worth capturing and analyzing at all, particularly in instances where enormous amounts of data are being generated.
The outcome of the local computations is a decision on how to act in case of a detected event. In some cases, the decision making is going to be affected by the feedback from the backend as a result of a long-term monitoring and prediction procedure of the whole system. The expected long-term outcome is to minimize the risk of infrastructure failure and accomplish an unobstructed operation.
Finally, the stakeholders can update the policy accordingly if needed and disseminate it in a top-bottom fashion though the IoT system. More specific, stakeholders such as IoT vendors or service providers can exploit the processed data in order e.g. to replace failed or malfunctioned IoT equipment which is critical for the smart infrastructure monitoring/prediction capabilities.
V. BUSINESS DECISION MAKING POLICY
The CE-IoT framework implements a utility-driven operation by exploiting the aforementioned smart sensing and data analysis procedures. A decision support system (DSS) is utilized for this purpose. The Analytic-Synthetic method, called Stochastic UTA (UTilites Additives – Additive utility) [40], evaluates and rates the alternative choices (Sell, Dispose, Repair). The utilization method is described below.
A. The CE decision making model
The presented stochastic method is used in the interconnected environment with sensors/monitors on the products sending data about their lifecycle to the backend. The CE-IoT collects information about the “health” of each product and diagnoses if it needs ‘repair’, ‘buy new’ or ‘sold as an asset to another consumer’. The products are considered as assets and can reentered to the CE with a price depending from the market request.
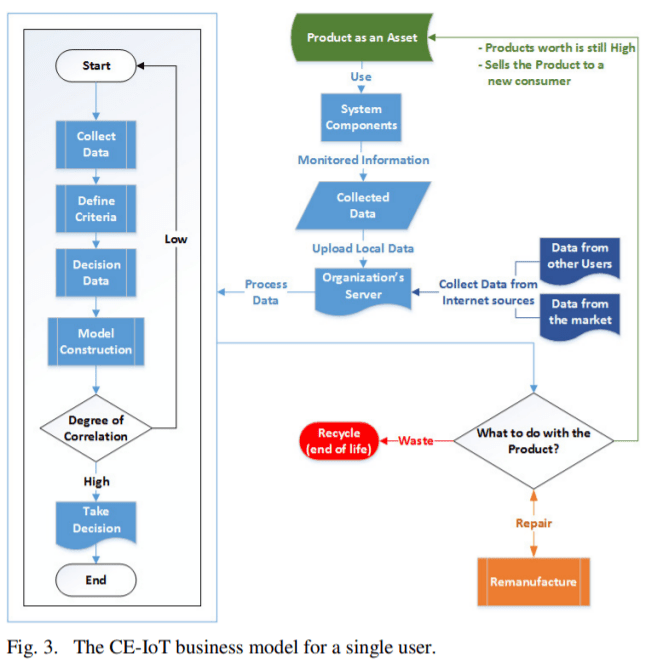
The CE-IoT agents send data to a server which also collects data from other CE users and from the market. These data are used by the DSS using the Analytic-Synthetic approach in which a Decision Maker has to take the Decision. As is shown in Fig. 3, a product is considered as an asset. The consumers/businesses buy this product due to their needs.
The Stochastic Method is applied when we want to create a Hierarchy Model for our decisions. The Stochastic UTA method implements this Analytic-Synthetic approach [40]. The philosophy of this approach in the context of the multi-criteria analysis lies in the estimation of a preference model, which
emerges as a conclusion from a given expression of the overall preference on alternative activities. The aim is to provide support for decision-making actions using operational models [41].
In the traditional form of the synthetic approach followed by the majority of the multi-criteria analysis problems, the composition model of the individual criteria is a priori known, while the overall preference is unknown [40].
The Stochastic UTA method exhibits the total utility of each of the three alternatives: sell, buy or repair. The decision maker takes the final decision about what to do with the product. Also, indexes are included that reveal the stability of the proposed model, like the Average Stability Index [40].
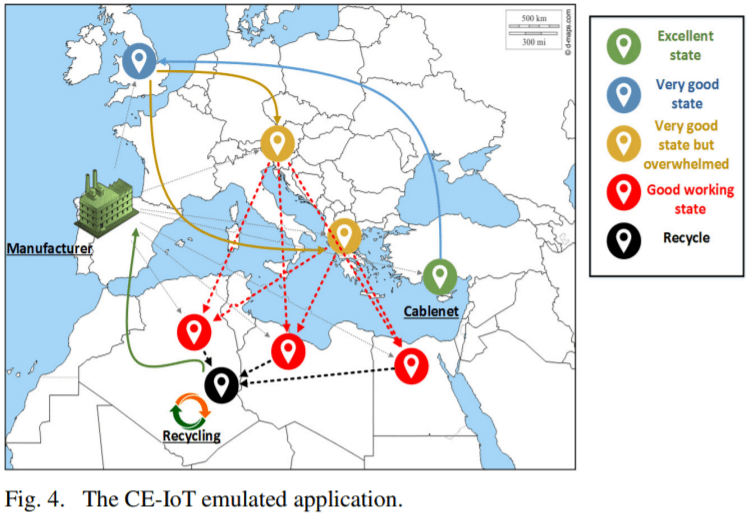
Fig. 4 illustrates an emulated iteration of the CE-IoT loop. As aforementioned our organization (Cablenet) uses its equipment to serve end-customers. When the system is upgraded, the related machinery is sold to start-ups in UK. Similarly, these companies can re-sell the CE assets when their utility goes beyond a threshold. Afterwards, the assets are gifted to third-world countries that use older technologies in their networks. When the products are no longer working, they are recycled in businesses that are close to these areas. Finally a subset of useful materials are exported back to the manufacturers and the loop starts again.
VI. CONCLUSION
The ongoing interplay of the CE and IoT sectors enables new business opportunities while promoting green technologies. This paper presents the CE-IoT framework, which forms an enhanced recycle-rewarding system for ICT organizations. Except from recycling, the overall approach extends the productive period of the electronic assets, enhances the e-waste management, and improves the economic operations of the involved stakeholders. A preliminary implementation on a real equipment is detailed, which also involves AI, ML, and DSSs. The CE-IoT is applied on a medium-size ICT provider and the overall trace of a real supply-chain scenario is described. The ML techniques promote green computing/networking policies on the organization that currently operates the valuable assets, while the AI and DSS procedures administrate the CE-IoT functionality and provide valuable insights for the decision making staff.
However, as the cooperating organizations exchange the CE assets, we need a transparent way to administrated and authorize the performed actions. Thus, the usage of blockchains as a distributed ledger that will maintain this information is considered as future work.
ACKNOWLEDGMENT
This work has received funding from the European Union Horizon’s 2020 research and innovation programme H2020- DS-SC7-2017, under grant agreement No. 786890 (THREATARREST), as well as the Marie Skodowska-Curie Actions (MSCA) Research and Innovation Staff Exchange (RISE), H2020-MSCA-RISE-2017, under grant agreements No. 777855 (CE-IoT) and No. 778229 (Ideal Cities).
REFERENCES
[1] C. M. Angelopoulos, S. Nikoletseas, and G. C. Theofanopoulos, “A smart system for garden watering using wireless sensor networks,” 9th MobiWac, ACM, Florida, USA, pp. 167-170, Nov. 2011.
[2] C. M. Angelopoulos, G. Filios, S. Nikoletseas, and D. Patroumpa, “A holistic IPv6 test-bed for smart, green buildings,” IEEE International Conference on Communications (ICC), IEEE, Budapest, Hungary, pp. 1- 12, Nov. 2013.
[3] Y. Kalmykova, M. Sadagopan, and L. Rosado, “Circular economy – From review of theories and practices to development of implementation tools,” Resources, Conservation and Recycling – Sustainable Resource Management and the Circular Economy, Elsevier, vol. 135, issue 1, pp. 190-201, Aug. 2018.
[4] A. Heshmati, “A review of the circular economy and its implementation,” International Journal of Green Economics, Inderscience, vol. 11, issue 3/4, pp. 251-288, Feb. 2018.
[5] A. Urbinati, D. Chiaroni, and V. Chiesa, “Towards a new taxonomy of circular economy business models,” Journal of Cleaner Production, Elsevier, vol. 168, issue 1, pp. 487-498, Dec. 2017.
[6] G. Schulze, “Growth Within: A Circular Economy Vision for a Competitive Europe,” Ellen MacArthur Foundation and the McKinsey Center for Business and Environment, pp. 1-22, Nov. 2016.
[7] J. Sarkis and H. Zhu, “Information technology and systems in China’s circular economy: implications for sustainability,” Journal of Systems and Information Technology, Emerald, vol. 10, issue 3, pp. 202-217, 2008.
[8] A. Khalamayzer, ‘7 companies advancing the circular economy by selling products as a service,’ GreenBiz, Feb. 2018, https://www.greenbiz.com/article/7-companies-offering-circulareconomy-service .
[9] I. Askoxylakis, “A framework for pairing circular economy and the Internet of Things,” IEEE International Conference on Communications (ICC), IEEE, Kansas City, MO, USA, May 2018.
[10] J. Soldatos, N. Kefalakis, M. Serrano, and M. Hauswirth, “Design principles for utility-driven services and cloud-based computing modelling for the Internet of Things,” International Journal of Web and Grid Services, Inderscience, vol. 10, issue 2-3, pp. 139-167, Mar. 2014.
[11] K. B. Slimane and D. Chaney, ‘Towards marketing of functionality: insights from Michelin and Hilti,’ Journal of Strategic Marketing, Taylor & Francis, vol. 23, issue 3, pp. 224-237, 2015.
[12] State of Green, “Circular consumption through innovative business models,” Nov. 2017, https://stateofgreen.com/en/partners/state-ofgreen/news/circular-consumption-through-innovative-business-models/ .
[13] K. Lyndegaard, ‘Combining spatial and network analysis: a case study of the GoMore network,’ Esri European User Conference (EUC), Esri, Split, Croatia, pp. 1-11, Oct. 2014.
[14] A. T. S. Worth and B. Escartin-Claveria, ‘Alstom’s approach to railway condition monitoring,’ 6th IET Conference on Railway Condition Monitoring (RCM), IET, Birmingham, UK, pp. 1-6, Sept., 2014.
[15] M. Orehek and C. Robl, ‘Model-based design of an ECU with data- and event-driven parts using auto code generetion,’ IEEE ICRA, IEEE, Seoul, South Korea, pp. 1346-1351, May 2001.
[16] Information & Communication Technology (ICT), 1st International Workshop on Green Wireless 2008 (W-GREEN), Lapland, Finland, 2008, https://www.cwc.oulu.fi/workshops/W-Green2008.pdf.
[17] sustainableIT, “Green computing makes good business sense,” 2011, https://www.sustainableit.com/green-computers-make-good-businesssense/.
[18] G. Cecere, N. Corrocher, C. Gossart, and M. Ozman, “Technological pervasiveness and variety of innovators in Green ICT: a patent-based analysis,” Research Policy, Elsevier, vol. 43, issue 10, pp. 1827-1839, Dec. 2014.
[19] Z. S. Andreopoulou, “Green Informatics: ICT for green and sustainability,” Agricultural Informatics, vol. 3, issue 2, pp. 1-8, Dec. 2012.
[20] A. Ozturk, K. Umit, I. T. Medeni, B. Ucuncu, M. Caylan, F. Akba, and T. D. Medeni, “Green ICT (Informaiton and Communication Technologies): a review of academic and practitioner perspectives,” International Journal of eBusiness and eGoverment Studies, The Social Sciences Research Society, vol. 3, issue 1, pp. 1-16, 2011.
[21] L.-D. Radu, “Determinants of green ICT adoption in organizations: a theoretical perspective,” Sustainability, MDPI, vol. 8, issue 8, article 731, pp. 1-16, Jul. 2016.
[22] X. Qiu, H. Luo, G. Xu, R. Zhong, and G. Q. Huang, “Physical assets and service sharing for IoT-enabled Supply Hub in Industrial Park (SHIP),” International Journal of Production Economics, Elsevier, vol. 159, issue 1, pp. 4-15, Jan. 2015.
[23] Z. Pang, Q. Chen, W. Han, and L. Zheng, “Value-centric design of the Internet-of-things solutions for food supply chain: value creation, sensor portfolio and information fusion,” Information Systems Frontiers, Springer, vol. 17, issue 2, pp. 29-319, Apr. 2015.
[24] A. Aminoff and O. Kettunen, “Sustainable supply chain management in a circular economy – towards supply circles,” International Conference on Sustainable Design and Manufacturing (SDM), Springer, SIST, vol. 52, pp. 61-72, Apr. 2016.
[25] G. Alexandris, S. Alexaki, V. Katos, and G. Hatzivasilis, “Blockchains as enablers for auditing cooperative circular economy networks,” 23rd International Workshop on Computer Aided Modeling and Design of Communicaiton Links and Networks (CAMAD), IEEE, Barcelona, Spain, pp. 1-7, Sept. 2018.
[26] J. Kallio, M. Antikainen, and O. Kettunen, “A tool rental service scenario,” 11th UBICOMM, Barcelona, Spain, pp. 60-65, Nov. 2017.
[27] A. M. Adeola and M. Othman, “An overview of ICT waste management,” 7th International Conference on Networked Computing, IEEE, Gyeongsangbuk-do, South Korea, pp. 109-115, Sep. 2011.
[28] M. H. Masud, N. B.T. A. Malik, and Md. K. Shukran, “Evaluating the effectiveness of energy efficient and eco-leveling ICT infrastructures for environmental sustainability,” 3rd International Conference on Engineering and ICT (ICEI), Melaka, Malaysia, pp. 1-5, Apr. 2012.
[29] J. Sanekata, M. Tani, T. Nishi, Y. Hamatsuka, and H. Sugai, “Environmental impact assessment logic for ICT systems named SILCA and its case example,” IEEE International Symposium on Electronics and the Environment, IEEE, Orlando, FL, USA, pp. 6-11, May 2007.
[30] K. Fysarakis, G. Hatzivasilis, I. Askoxylakis, and C. Manifavas, “RTSPDM: Real-Time Security, Privacy and Dependability Management of Heterogeneous Systems,” In: Tryfonas T., Askoxylakis I. (eds) Human Aspects of Information Security, Privacy, and Trust. HAS 2015. Lecture Notes in Computer Science, vol 9190. Springer, Cham, pp. 619–630, 2015.
[31] K. Fysarakis, G. Hatzivasilis, C. Manifavas, and I. Papaefstathiou, “RtVMF: A Secure Real-Time Vehicle Management Framework,” IEEE Pervasive Comput., vol. 15, no. 1, pp. 22–30, Jan. 2016.
[32] G. Hatzivasilis, I. Papaefstathiou, D. Plexousakis, C. Manifavas, and N. Papadakis, “AmbISPDM: managing embedded systems in ambient environment and disaster mitigation planning,” Applied Intelligence, Springer, pp. 1–21, 2017.
[33] JADE framework: https://jade.tilab.com/
[34] T. Patkos and D. Pleousakis, “DECKT: epistemic reasoning for ambient intelligence,” ERCIM News magazine, Special Theme: Intelligent and Cognitive Systems, vol. 2011, issue 84, pp. 1-30, Jan. 2011.
[35] FIPA ACL: www.fipa.org/repository/aclspecs.html .
[36] P. V. Klaine, M. A. Imran, O. Onireti, and R, D. Souza, “A survey of machine learning techniques applied to self-organizing cellular networks,” IEEE Communications Surveys & Tutorials, IEEE, vol. 19, issue 4, pp. 2392-2431, Oct. 2017.
[37] P. Stone and M. Veloso, “Multiagent systems: a survey from a machine learning perspective,” Autonomous Robots, Springer, vol. 8, issue 3, pp. 345-383, June 2000.
[38] M. Langkvist, L. Karlsson, and A. Loutfi, “A review of unsurpervised feature learning and deep learning for time-series modeling,” Pattern Recognition Letters, Elsevier, vol. 42, issue 1, pp. 11-24, June 2014.
[39] S. B. Kotsiantis, I. D. Zaharakis, and P. E. Pintelas, “Machine learning: a review of classification and combining techniques,” Artificial Intelligence Review, vol. 26, issue 3, pp. 159-190, Nov. 2006.
[40] E. Grigoroudis and Y. Siskos, “Customer satisfaction evaluation,” International Series in Operations Research & Management Science, Springer, vol 139, pp. 1-308, 2010.
[41] E. Jacquet-Lagreze and Y. Siskos, “Preference disaggregation: 20 years of MCDA experiene,” European Journal of Operational Research, Elsevier, vol. 130, issue 2, pp. 233-245, Apr. 2001.
























































































































0 Comments