Vehicular Ad hoc NETworks (VANET) are becoming popular due to the emergence of the Internet of Things and ambient intelligence applications. In such networks, secure resource sharing functionality is accomplished by incorporating trust schemes. Current solutions adopt peer-to-peer technologies that can cover the large operational area. However, these systems fail to capture some inherent properties of VANETs, such as fast and ephemeral interaction, making robust trust evaluation of crowdsourcing challenges. In this article, we propose MobileTrust – a hybrid trust-based system for secure resource sharing in VANETs. The proposal is a breakthrough in centralized trust computing that utilizes cloud and upcoming 5G technologies in order to provide robust trust establishment with global scalability. The ad hoc communication is energy-efficient and protects the system against threats that are not countered by the current settings. To evaluate its performance and effectiveness, MobileTrust is modelled in the SUMO simulator and tested on the traffic features of the small-size German city of Eichstatt. Similar schemes are implemented in the same platform in order to provide a fair comparison. Moreover, MobileTrust is deployed on a typical embedded system platform and applied on a real smart car installation for monitoring traffic and road-state parameters of an urban application. The proposed system is developed under the EU-founded THREAT-ARREST project, to provide security, privacy, and trust in an intelligent and energy-aware transportation scenario, bringing closer the vision of a sustainable circular economy.
CCS Concepts:• Security and privacy → Trust frameworks • Networks → Network security • Networks → Network privacy and anonymity • Networks → Network mobility • Networks → Cyberphysical networks • Networks → Cloud computing
1 INTRODUCTION
In this era of the 4th Industrial revolution, Internet-of-Things (IoT) applications influence our daily activities, with the cyber-physical systems (CPS) market value reaching 8,120 million dollars in 2021 [1]. Vehicular Ad hoc NETworks (VANETs) constitute a special type of mobile networking in this domain [2], [3], [4], [5]. They include vehicle-to-vehicle (V2V) and vehicle-to roadside infrastructure (V2I) communication for providing, among others, traffic information, navigation, safety, or other services [6], [7].
In recent year, several circular economy (CE) initiatives are emerging, penetrating also in the VANET domain. Quality-of-Service (QoS) and energy-aware solutions that serve numerous users and devices, enhance the design perspectives towards CE, creating looping assets and maximizing the utilization of resources, like ridesharing [8]. Other interesting proposals for intelligent transportation include smart traffic control, ride service hailing, or even car-sharing.
The USA standard IEEE 1609 Wireless Access in Vehicular Environments (WAVE) is built on IEEE 802.11p [9], [10]. It operates in 5.9 GHz frequency and supports multi-channel communication, security, and lightweight application layer protocols. The relevant European standard ETSI ITS G5 [11] operates in the same band, implementing multi-radio multi-channel functionality, security, and a complex hierarchy of higher layer protocols that integrate a broad range of main services.
This paper focuses on the security aspects of VANET ecosystems. The aforementioned standards cover coarse and generic security services where
cryptographic primitives are utilized to accomplish the properties of authentication, authorization, confidentiality, and integrity. However, the VANET problem domain constitutes a field of security challenges arising from the violation of the fair use by selfish or malicious participants [12]. Selfish entities may attempt to avoid the additional computational or communication effort from contributing to the collective operations of the social network. Malicious entities exploit the system’s vulnerabilities and rating mechanisms to launch attacks, like Denial of Service (DoS), Byzantine failures, or interception of normal interaction by injecting fake information.
As such, a trust-based computing approach must be adopted [13], [14]. The underlying techniques aim to evaluate the participants’ activity in order to detect security policy violation attempts and in which case countermeasures would be forced that restrict or ban the involving entities. The goal is to encourage the legitimate nodes in keeping up with their positive contribution, discourage and penalise the selfish and malicious participants from misbehaving, and protect the whole infrastructure from attacks.
This paper presents a trust-based resource sharing system for VANETS, called MobileTrust. The system is built upon the aforementioned main security functionality (i.e. IEEE 802.11p[10], ETSI ITS G5[11]) and its main contribution is to evaluate the entities’ behavioronce the cryptographically secure communication is achieved. As a case study, we considered the scenario where vehicles and smart city infrastructure components exchange information regarding traffic congestion and other road events. A simulation study is conducted in the Simulation of Urban MObility (SUMO) for the evaluation of the main protection and performance properties of our proposal, and the comparison with relevant systems under the same setting. A real implementation is also deployed on embedded devices and Android smartphones that emulate the sensors and the communication equipment of a smart vehicle.
The remainder of the paper is organized as follows. Section 2 discusses the related work in the domain. Section 3 presents MobileTrust. Section 4 describes the theoretic analysis. Sections 5 shows the simulation analysis and the comparison of our proposal with the current solutions. Section 6 details the real implementation of MobileTrust on embedded devices. Finally, Section 7 concludes and refers to future work.
2 RELATED WORK
In the context of VANETs, trust-based interactions occur at high speeds and short time periods [13]. The knowledge integration algorithm should exhibit low complexity constraints, such as effective throughput, fast memory access, and costefficient processing. Scalability is a main concern, as incidents or road events could be reported either by single mobile nodes or by multiple vehicles.
General attacks on mobile ad hoc networks are surveyed in [15] and [16]. Furthermore, VANETs are vulnerable to false positioning, message modification, false message sending, and DoS [14]. Trust-based schemes are deployed as a main countermeasure against most of these threats. Inevitably, the formal trust evaluation processes are targeted by more sophisticated attackers [17]. The involved challenges of trust management in VANETs are reviewed in [18] and [19].
2.1 Trust-Based Resource Management
Several trust-based schemes have been proposed in the literature attempting to tackle resource management. For this study, we focus on these systems that collect and process information in real-time for a VANET setting.
The Vehicle Ad hoc network Reputation System (VARS) [20] is one of the first attempts to incorporate trust-based computing in the field of VANETs. It forms a modular and peer-to-peer (P2P) reputation system that separates direct and indirect information when integrating knowledge. The system rests its confidence on the distributed content itself rather on the node behavior. The forwarding nodes attach in the transmitted message their opinion about the content (e.g. traffic congestion on a road segment or blocked route). The receiver utilizes the contextualized data to evaluate the trustworthiness of the message. A node’s opinion about an event can be formed by direct knowledge, indirect knowledge sent by a known sender, partially by the attached opinions on the message by the forwarding nodes, or by a combination of all these interactions. A main performance drawback of VARS is the fact that the communication bandwidth is substantially affected due to the overheads from the information that is cumulatively appended along the communication path when a high number of forwarding nodes is involved. Furthermore, the proposed approach does not enforce authentication, thus making the system vulnerable to attacks from simple modification to complete deletion of messages.
The Event-based Reputation System (ERS) [21] attempts to detect inaccurate traffic events and deter attackers from spreading false messages. Traffic information is collected from the vehicles and the road infrastructure. The system utilizes distributed observations and tries to figure out if a traffic event really exits and how long it lasts. The information of an event is maintained in a table by every vehicle that becomes aware of the incident, either by direct interaction or indirect notifications. The event table stores data regarding the event’s identity, type, occurrence, location, message transmission range, reputation, and indirect confidence list. One main scalability problem that arises is the difficulty in managing the confidence lists for all events that are reported in the network. Also, the simple evaluation process of indirect notifications makes the system vulnerable to attackers that perform badmouthing (advertise bad recommendations for legitimate nodes) and ballot-stuffing (gain good reports from colluding malicious entities) [17]. Moreover, as ERS requires a significant amount of contributions in order to designate that an event has occurred, it fails when it comes to the early and timely notification of drivers regarding the existence of an accident on the road ahead. However, the safety of drivers is an essential goal towards the real deployment of VANETs ([18], [19]).
The Trust Based Security Enhancement (TBSE) for VANETs [22] is designed upon the core cryptographic techniques and acts as a second defense mechanism against inside attackers. Both direct and indirect knowledge are utilized for the trust estimations. Direct interaction is evaluated based on the Bayesian rule. For the rating of the third-party recommendations, the DempsterShafer Theory (DST) [23] is employed, allowing the probabilistic assessment of the truthfulness of an event in the presence of uncertainty. Then, the calculated trust values are stored in a repository where upper layer applications can gain access and utilize this information in order to achieve their security goals, like secure resource sharing or routing. However, the attacker model is restricted to a low number of malicious entities that do not collude with each other. Passive attacks are also not studied. Moreover, TBSE is vulnerable to information cascading and oversampling [24]. In cascading, a decision is madeby the nodes deciding sequentially after observing the behavior of the other participants. Therefore, a node’s choice is highly influenced by the previous decisions that can
overrule its own observation. Oversampling occurs when a node receives the opinion of nodes i and j, but j’s opinion has been initially influenced by the decision of i. Thus, the contributing information by j is oversampled.
A Social Network approach to Trust Management (SNTM) in VANETs is presented in [24]. The main contribution of this study is the limitation of the bad effects from information cascading and oversampling in P2P communication. SNTM tackles directly cascading by assigning higher voting weight to the vehicles that are closer to the event. As the influence from cascading is eliminated and the result becomes more accurate, the potential oversampling is also limited indirectly. The nodes also attach their opinion regarding an event in the message. The receivers contrast this knowledge with their own opinion. Then, they rate the other contributors and estimate the message’s quality.
2.2 Discussion
Centralized trust evaluation was not considered an appropriate architecture for VANETs by the research community due to scalability issues attributed to the high the computational and communicational burden on a central entity, as well as dependability concerns as this central entity would be a single point of failure [24]. The design of P2P architectures seemed as a oneway approach towards the establishment of mobile trust. All the aforementioned related works promote the P2P paradigm. However, in order to build effective and trustworthy P2P relationships, one would need a significant and frequent amount of interactions between the peers. Thus, these studies fail to capture some inherent properties of VANETs. The ephemeral nature of such networks does not veritably facilitate the P2P trust. Moreover, trust is not necessarily transitive and the gathering of information from past interaction, by each peer for every other participant, is computationally expensive and even impossible under realistic assumptions. As the vehicles drive in high speeds, when the selection and processing of the proper knowledge for an event are completed, the outcome is no longer required, as the vehicle has either faced, dealt with or bypassed the reported problem. P2P trust will inevitably become vulnerable to information cascading and oversampling in an actual setting.
Authentication and cryptographic security is another important issue. A number of studies (e.g. [20], [21]) ignored or overlooked the implications of cryptographic communication and the overheads from supporting this essential functionality in P2P networks. On the other hand, when peer authentication is implemented, privacy issues arise as a vehicle publishes data regarding its driving route or other user sensitive information [25].
The evolution of cloud computing and the upcoming 5G technologies, like Multiaccess Edge Computing (MEC) [26], [27] can help towards overcoming the restrictions of both centralized and P2P trust in the VANETs domain. This study proposes a hybrid trust algorithm where both types of interaction are utilized. Theoretical results regarding the scalability of hybrid P2P systems for data distribution are reported in [28]. The core trust calculation and maintenance is performed in a centralized manner, focusing equally on the data correctness and the evaluation of the nodes’ behavior. Nevertheless, the obstacles of centralized knowledge integration are overcome by distributing and parallelizing the related computations in the cloud and MEC. The internal computations are further parallelized in Graphics Processing Units (GPUs), enhancing the overall performance.
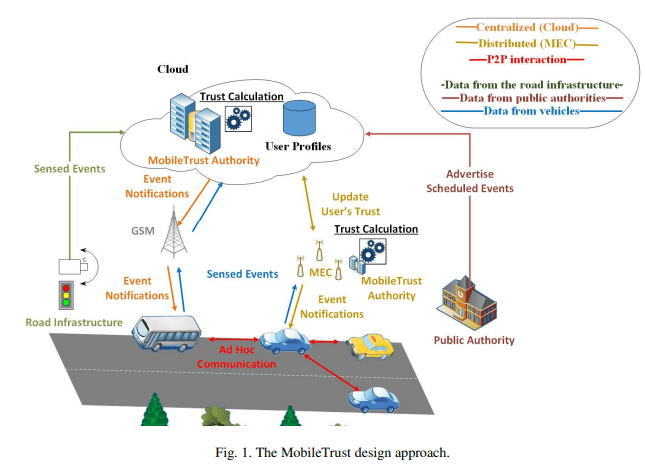
Authenticated users contribute with first-hand observations. Only the central authority integrates this knowledge and reports the existing road events, eliminating the bad effects of cascading and oversampling. In order to decrease the centralized communication, the peers can broadcast this timely- and spatial-sensitive data that are digitally signed by the authority, without requiring to authenticate each other, and thus, preserving their privacy between the vehicle nodes. Fig. 1 illustrates the proposed setting. In short, the proposed MobileTrust system aims to offer:
- Efficient centralized knowledge integration, exploiting the capabilities of cloud
computing, MEC, and GPUs - Effective trust computation of authenticated users in a centralized manner,
capturing the inheriting properties of VANETs (e.g. ephemeral environment, timesensitive information, different sensing capabilities, and safety response) - High accuracy in estimating the presence of a road event, even in the presence of
malicious entities - Preservation of P2P privacy
- Secure cryptographic communication in all transactions
- DoS resilience
The overall setting provides efficient, effective, and timely accurate information, countering a high variety of attacks and offering secure and privacy-preserving communication.
3 MobileTrust
This section details the MobileTrust design. The system integrates first-hand information from the involving participants. The trustworthiness of each contributing node is taken into consideration during this process. The contributors are authenticated while privacy is preserved in the P2P interaction. The overall setting presupposes that there exists a safe procedure to register/identify the participating vehicles in order to prevent the attackers from introducing virtual vehicles that transmit bogus data. The potential towards global scalability is also presented. The assignment of the constant coefficients for the reputation and trust computations (e.g. the reputation rating values or the trust integrating weights) is based on relevant studies ([20], [21], [22], [24]) and in a previous analysis that the authors have conducted under a similar setting [37].
3.1 Knowledge Integration
3.1 Knowledge Integration Three reputation resources are considered by direct interaction, notices send by trustworthy public authorities, and notifications made by a centralized entity. The following event types (E) are modelled: i) Road accidents, ii) Traffic congestion, iii) Bad road conditions, iv) Working activities, v) Protest, ceremony, military, religious, athletic, or other march, vi) Route diversion by police, vii) Blocked road (i.e. by physical obstacle), viii) General alarm to draw the drivers’ attention and be cautious.
When a major event is reported, the nodes that are located closer and reckoned sooner can contribute with data having a higher level of accuracy. These advantageous geo location reporters gain higher reputation values if the transmitted data is confirmed.
Based on the evaluation result, a message can be rejected, accepted but not integrated, or accepted and integrated. Messages originating from untrusted nodes or those who report events that are not close to the nodes’ location are rejected and the involving nodes are rated negatively.
For the traffic report application, the vehicles must collect information regarding their speed. The road routes are segmented, for example every 500m. A vehicle calculates its average speed in each crossed segment. If the speed falls under a threshold, the vehicle indicates the segment as congested. When a decent amount of similar indications are received by the backend component (see the text below), the application reports the traffic congestion. If there are no incoming indications, the congestion report for a segment fades as time elapses, until it is assigned as normal again. MobileTrust bounds the misbehavior of a malicious vehicle from arbitrarily reporting segments as congested. The attacker will be rated negatively as long as his indications will not be supported by other participants.
The events of working activities, protest or other marches, route diversion by the police, blocked road segment, or general alarm are manually designated by the driver. Moreover, the backend application can be informed in advance for such events by the involving authorities, which are considered trustworthy. For example, the municipality can report the scheduled working activities or athletic events, which are then imported into the system. The centralized trust management component performs the following steps:
- The first notification of an event ∈ E on a road section rs creates a new event entry with neutral confidence (the value depends on the node’s overall trustworthiness and its reputation in observing the specific event type).
- As other nodes located in the same road section advocate that the event is ongoing (by sending the same notification type as in step 1), the confidence that the event is actually happening increases.
- The confidence Crse is calculated as the ratio of the contributing nodes (contrrs,e) to the nodes that enter the road section (passingrs). It is defined in (1) as:
- Incoming vehicles are notified about the active events in advance, before entering the road section. The reported event’s confidence fades as time elapses and no new notifications are made, to designate that the event is smoothing out (i.e. 10% decrement for every minute that passes while the incoming vehicles do not notice the event).
- The event entry is terminated after a fixed-time period (i.e. 5 minutes) to prevent the case where an attacker sends the same notification over and over in order to keep the entry active.
- Then, the nodes that cross the road section are evaluated. The nodes gain a reputation rate according to the events maximum level of confidence that was achieved during the active period.
a.The contributing nodes gain negative (-4), neutral (0), and positive (+1) reputation values r for low, moderate, and high level of confidence, respectively. In the last case, the first responders (2% of the total contributors) are awarded an extra bonus score (+1).
b. Similarly, the non-contributing nodes are rated negatively (-4) if the event gained moderate or high confidence (based on equation (1)) in order to detect selfish nodes, otherwise they are ranked neutrally (0).
c. Also, the system ranks negatively (-4) the nodes that remain constantly in a road segment and report events (i.e. traffic jam) while the majority of the entering nodes continue their route, in an attempt to force the malicious nodes to be in continuous move and be unable to target distinct road segments. - If notifications are sent after the active period, a new event entry is created (step 1).
3.2 The Trust Framework
For every user, MobileTrust evaluates his/hers trustworthiness based on the past interaction. All new users start with neutral trust and reputation values (0), which are continuously updated as new pieces of knowledge are integrated.
MobileTrust maintains a small history of the latest evaluation results for each event type. The history size (he) is determined by the event’s frequency, ranging from 500 ranks for traffic monitoring to 30 ranks for the user defined reports (e.g. blocked road segments or protest march). Reputation fading is applied for each event type, based on a beta distribution [29], by assigning higher weights (fading_wi) to the most recent interactions. The reputation value of the user for a specific event type, R(User, e), is the average weighted summation of the relevant historical values, as defined in
(2):
This information determines the effectiveness of a user in reporting a specific type of event. Thus, the system can discriminate the different sensing capabilities of the various nodes and exploit this knowledge (if the reputation value is for example >0.5), especially when an event has been just reported or in road segments with few contributors. Moreover, the system can detect a malfunction in the sensing equipment or a malicious activity that tries to manipulate the rating mechanism for a specific event type (i.e. when the reputation value decreases beyond a threshold of 0.4) and not integrate the relevant contributions.
Trust estimates the overall cooperativeness of a user. Each event reputation gains a weight (we) based on the event’s frequency and severity. Traffic monitoring and road accident reports are assigned with a weight of 0.30 and the rest types are assigned with a weight of 0.1 (the weights summation is equal to 1.0). The trustworthiness for a user, TUser, is then calculated by aggregating the underlying reputation values, as defined in
(3):
A user with a trust level that exceeds 0.8 or 0.6 is considered trusted and legitimate, respectively. When the trust falls beyond a threshold (i.e. ≤0.5), the user is notified for his/hers misbehavior and is categorized as suspicious. If the cooperation level keeps degrading (i.e. ≤0.4), the node is finally reported as malicious and is expelled from the network.
3.3 Authentication and Privacy
In order to maintain the reputation records and operate in a trustworthy manner, the users that contribute information to MobileTrust must be authenticated. Each driver creates an account with a username/password pair (or other mean of authentication, like near-field communication (NFC), Bluetooth pairing, etc.) and logs on the system through the vehicle’s infotainment system (SSL/TLS communication). Only authenticated users can send information to the application through a secure channel. The data are encrypted with a symmetric session key (such as AES) and through an appropriate protocol such as SSL/TLS.
Furthermore, passive anonymous use is also supported. The notifications that are reported by MobileTrust are signed with the authority’s private asymmetric key (RSA). To reserve resources, all active notifications for a road segment are included in the signed message. Thus, every node can verify the central authority, as its public asymmetric key is known to all participants. However, it should be stated that a high volume of anonymous users who do not contribute with any information, could degrade the effectiveness of the system in the presence of attackers (as detailed in the theoretic analysis subsection 4.2).
A main contribution of the overall setting is the privacy protection of the V2V interaction. In order to preserve privacy, the nodes exchange only the publicly-signed notifications. Thus, if a vehicle requests information regarding some road segments, the other vehicles or the road infrastructure will respond with the relevant messages that have been previously retrieved by the central authority, without requiring to authenticate each other. Both the request and the response are broadcasted messages in a P2P communication of the nearby nodes.
The notification format, as described in (4), is consisted of the road segment’s ID, the event type, the date (timestamp) where the event occurred, and a sequence number (bounded to a specific segment ID and event type, and initialized every day when the date is changed). This information is both included in the encrypted data and also sent in plaintext along with the rest of the message. To preserve resources, the nodes maintain only the latest notifications of each event type for a road segment. Moreover, a node deletes the older messages of passed segments as time elapses and the events’ active period terminates (i.e. after 5 minutes) in order to keep the memory usage profile low
Notification format:
[Road segment ID | Event type | Date | Sequence no.]
The plaintext notification identifier is utilized as an automatic access control tag to degrade the effectiveness of DoS attacks at the responder and requester ends. A request message is unencrypted and contains road segment IDs. The responder examines the included road segment IDs and broadcasts the latest related notifications. If irrelevant segments are included, the node discards the message and does not proceed in any further actions. The node also adheres to a threshold for a maximum number of request responds in the current time window (i.e. at most ten responds per minute) as an additional measure against DoS by bogus request messages.
A response message replays the public notifications, as they were retrieved by the central authority. For each incoming response, the requester examines the plaintext notification identifier. The node automatically recognizes the relevant notifications by examining the road segment ID and the timestamp. Then, it checks the sequence number and evaluates the newest notification version. The node decrypts the message with the authority’s public key. If the decryption and the integrity check (SHA512) are successful, the node integrates the notification. Otherwise, the node proceeds to the older received versions of the notification. However, an attacker can still send erroneous messages with a valid notification identifier and a high sequence number in order to enforce the requester to perform the decryption operation. Thus, if several decryption attempts fail in a time interval (e.g. five fails in the last minute), the node turns in back-off mode for a while, until the vehicle drives away from the region. The user can later login the system and report the road segments where the malicious activity was observed.
3.4 Vehicle Registration
Except from authenticating the active users through the proposed application, we must also enforce a procedure to examine that he/she is driving a real vehicle. Otherwise, a malicious entity could create several user accounts for virtual vehicles, which would later launch coordinated sophisticated attacks on-line by sending fake positioning information along with erroneous road events. This is a general problem that affects all VANET settings (e.g.[20], [21], [22], [24]). An indicative case is the money laundering scam in Uber. Collaborating drivers log in the system through a virtual machine (VM) which emulates a fake-GPS service. Users/payers find these taxicabs via specific marketplaces in the dark-web and hire services that they do not actually use, laundering money in the process.
Identification and authentication of a vehicle is out of scope for this study and MobileTrust presupposes that the smart vehicle industry will deploy such an identification mechanism. Nonetheless, a basic protection approach is sketched. Each manufacturer nowadays assigns a unique identifier for each produced vehicle, known as the Vehicle Identification Number (VIN) . VIN is composed of 17 digits and acts as the vehicle’s fingerprint. For the modern smart functionality, the manufacturer (or another trusted party) can sign and provide the vehicle owner with a digital certificate. The certificate will contain VIN and other vehicle-related information. Then, MobileTrust or other smart applications can obtain this data through the user’s equipment and check the existence of the mobile node. The application can also interact with the signing entity in order to evaluate the certification’s validity (e.g. if it has been revoked). Except VIN, if the vehicle is equipped with a modern Electronic License Plate (ELP) , the related data could be also utilized for the same purpose.
The overall process can be further enhanced with the analysis that is performed by popular Internet services and social media (i.e. Gmail and Facebook). For security purposes, they can record the set of devices with which the user usually logs onto the system and try to keep out intruders that have disclosed the user’s credentials.
3.5 Towards Global Scalability
Centralized architectures were considered, in general, disadvantageous in comparison to P2P settings, as they constitute a single point of processing and a bottleneck [13], [24]. However, cloud and fog computing is now providing several solutions regarding efficiency and dependability [30].
The component of MobileTrust that performs all the computational intensive operations is the central authority. Nevertheless, VANETs and the proposed trust algorithm exhibit some inherited design properties that enable distribution, parallelization and global scalability. First of all, each authenticated user/driver is located in a specific region at each time point, and, usually, drives around a particular geographic location most of the time. Secondly, the processed data are region dependent. Thus, the knowledge integration of each road segment can be parallelized in a finegrained manner.
The IT industry that provides cloud services installs several datacenters in each continent around the globe. The application traffic is routed to the nearest datacenter based on the IP address. Load balancing among the datacenters is delivered by the cloud provider [31]. Thus, the traffic from a country is transmitted to specific datacenters. The user data can be also maintained in an efficient and distributed manner in the cloud, similarly to an email service, a social network, or other globalscale applications [32].
The MobileTrust data gathering and integration algorithm can be further parallelized based on the road segments. Each hired parallel processing unit in a datacenter can perform the trust computations of a single or a group of nearby road segments. The processing units can read data from a pool and serve the incoming traffic completely independent from each other. Each core processes data buckets, where each bucket contains the information for a distinct event entry. As mentioned earlier, the event entries in a road segment remain active for a fixed-time period, for example 5 minutes. Then, the core updates the trust profiles of the contributing users. GPUprocessing can decrease the overall processing time.
Additionally, MEC technologies [26] can further reduce the communication delay. The parallel processing can be installed closer to the smart road infrastructure and drastically reduce the round-trip time (Fig. 1).
4 THEORETIC ANALYSIS
This section details the theoretical analysis of the proposed approach and its effectiveness in countering the attacker models that are detailed in the simulation study (Section 5). The overall analysis is based on the ordinary assumption that the mainstream cryptographic primitives (i.e. TLS, RSA, AES, and SHA512) are implemented and configured properly, and thus, their usage is considered theoretically secure. At first, we examine the security aspects that are provided by the deployed communication protocols. Then, we give proofs regarding the capabilities of MobileTrust in supporting the legitimate functionality in presence of attackers.
4.1 Protocol Analysis
The theoretic security analysis of the communication links between the involved entities and the MobileTrust component is modelled in the verification tool ProVerif [33] (the code is not included for brevity). It is a widely-used automatic symbolic protocol verifier that proves the security properties of the examined protocol, like authentication, secrecy, and adversary equivalence aspects. The examined protocol is modelled in a process calculus and is automatically translated in Horn clauses [33]. The tool resolves these clauses and determines if the security properties hold or not. In case where all properties are validated, ProVerif returns “true”. Otherwise, it outputs the properties that could not be satisfied. Three communication protocols are examined:
1. The user/vehicle login and knowledge transfer towards the Central Authority (CA)
2. Road segment notification requests from a vehicle to the CA
3. Road segment notification requests from a vehicle to another vehicle (P2P)
4.1.1 User login and contribution. In order to actively participate in the MobileTrust community, the driver has to authenticate him/herself and enter the system. This includes an ordinary login process where the user inputs a pair of username/password through a SSL/TLS connection via HTTPS [34]. The CA safely receives the data and verifies the user.
The communication is initiated by the user. The user application and the CA perform the TLS handshake phase. The application obtains the CA’s digital certificate (X.509) and validates it. The two entities agree upon a randomly generated symmetric session key.
From this point on, the transmitted data are encrypted with the common key as in the TLS record phase. The user is prompted to provide his/hers data (e.g. [35]). The login request contains the user’s credentials (e.g. username, password’s digest, etc.). The CA decrypts it, checks the message’s integrity (HMAC-SHA256) and uniqueness, and contrasts the received information with the credentials that are maintained in an internal database. If the process is successful, the user is authenticated and can upload the evidence for ongoing road events. Then, the CA performs MobileTrust and evaluates the user’s cooperation. Fig. 2 depicts the communication steps.
The two entities began with the establishment of the secure channel (HTTPS/TLS handshake). Then, they utilized the derived session key and encrypt the rest exchanged messages (TLS record). ProVerif evaluates the abovementioned protocol steps (TLS phases and the transmission of the sensed data from the user to the CA) and validates that the overall setting offers authentication, confidentiality, integrity, and immunity to replay attacks.
4.1.2 Notification requests. Every user can ask the CA for the active event notification list of specific neighboring road segments. If the user is logged in, then the communication can be encrypted by the session key. Otherwise, the user can make unauthenticated requests and retain his/her privacy.
The request contains the required road segment ids and is encrypted with the CA’s public key. The digest of the data is also computed (SHA512) and the message is sent to the CA. The CA verifies the message’s integrity. The response contains the relevant notification list and a random nonce. The data digest is computed and then signed with CA’s private key. The user re-computes the digest of the received data and decrypts the signature with the CA’s public key. Fig. 3 illustrates the exchanged messages.
ProVerif validates that the communication is safe and provides CA authentication, integrity, and immunity to replay attacks. As described in the previous sections, full protection is not required here, as the road event notifications are meant to be publicly available.
4.1.3 P2P interaction. Nevertheless, a vehicle can request information about the neighboring road segments by the nearby vehicles. The requester sends the segment id list in plaintext along with the message’s digest. The contributors check the message’s integrity and respond with the related active notifications that they possess. The requester verifies the received notifications’ legitimacy as in the previous case. The protocol’s phases are similar with the relevant steps that are depicted in the second part of Fig. 3 for the anonymous communication between the user and the CA, with the initial request being an unencrypted broadcast message.
As before, the tool verifies that the interaction accomplishes the CA authentication, integrity, and immunity to replay attacks. Moreover, the contributors’ privacy is retained as no user- /vehicle-related data is disclosed.
4.2 Attack Mitigation
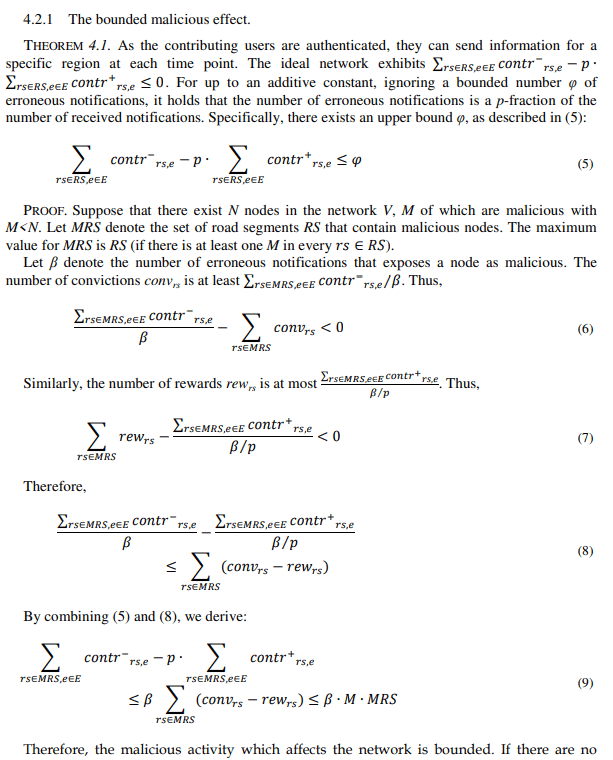
The theoretical security analysis of the trust computing mechanisms and its effectiveness in constraining the malicious activity is performed in two steps. First, we prove that the integration of malicious knowledge is bounded (Theorem 4.1). Then, we argue that MobileTrust’s efficacy is strongly related to the active participation of legitimate users (Lemma 4.1 and Theorem 4.2). The proposed defense mechanism increases significantly the effort that must be devoted by the attacker in order to exploit the system (Lemma 4.2). Finally, we evince that the system can provide protection even without the full participation of all legitimate users that may want to retain their privacy (Lemma 4.3).
For the system model, we form a VANET with N nodes, such as V={1, 2, …, N}. It is assumed that all links are bidirectional. If node I can receive packets that are directly transmitted by node j, then node j can receive packets that are directly transmitted by node i. The nodes are either vehicles or smart road infrastructure. Since the majority of these nodes are vehicles, the network dynamics are characterized by confined mobility, high speeds, and thus, short connection times between the nodes. The operational area can be very large, but the V2V communications are mainly local and the currently processed information for each node concerns specific road segments and not the whole network. Information regarding the examined road events is collected and exchanged by each node, either with other nodes or with the CA. Vehicles can travel freely, but in most cases, they have a relatively fixed route, such as buses.
Due to the complexity of a VANET system, several types of attacks can be performed. For the adversary model, we consider that attackers are internal nodes (malicious or compromised) that send out fraudulent event messages: they notify unreal events (i.e. traffic jam while the road segment is not congested) and if an event exists, they do not send any message to the authority denoting the incident (mislead the trust mechanism into producing false negatives in the case where a smaller number of legitimate nodes have reported the events). They are global attackers (have an overall coverage of the network and can eavesdrop on every message diffused by any vehicle), who can be either active or passive. Legitimate nodes can also malfunction with a low probability and perform the same actions for a while (i.e. Byzantine faults [36]). We start by providing some definitions and then the theorems and the proofs.
PROOF. Taking into account privacy issues and the user’s convenience, MobileTrust preconceives that users will not be always participating actively in the crowdsourcing activities. From THEOREM 4.2 it is derived that if the low volume of periodically malfunctioning legitimate modes along with the malicious ones does not constitute the majority, there exists a threshold of non-contributing users (NC-Userthr) where the system continues deducing the actual events’ status while retaining its capability in detecting/mitigating the erroneous functionality.
5 SIMULATION STUDY
This section presents the simulation evaluation of MobileTrust and other related trust schemes(Vehicle Ad hoc network Reputation System (VARS) [20], Event-based Reputation System (ERS) [21], Trust Based Security Enhancement (TBSE) [22], and Social Network approach to Trust Management (SNTM) [24]) over a common setting for VANET communication, under normal operation and two attack scenarios. As the theoretical analysis results provoke, we test the MobileTrust’s defense effectiveness for different ratios of contributing/malicious nodes.
5.1 Network Assumptions and Simulation Setup
Regarding the network assumptions, this study concentrates on VANETs and other similar mobile ad hoc networks. Attacks on resource management are mainly studied. MobileTrust is modelled in the SUMO and is implemented in C++. As aforementioned, the assignment of the constant coefficients for the reputation and trust elements is based on relevant studies ([20], [21], [22], [24]) and in a previous analysis by the authors [37]. Fig. 4 illustrates the simulation test for the map of Eichstatt, a small size city with around 13,000 citizens. The simulated area covers 4.5km×3.0km. For the evaluation of the different schemes, a VANET of 1500 nodes is modelled. The vehicles’ top speed varies from 18-80 km/h. There are utilized the propagation model two-ray ground reflection and the IEEE 802.11p [10] as the MAC layer. Each node has a 2Mbps raw bandwidth with 100m physical radio range. Table 1 summarizes the simulation parameters.
The experiments include an initialization and an evaluation phase. At first, nodes start communicating with the default values of each scheme. Then, the normal operation and two attack scenarios are evaluated, measuring the overall performance and security, respectively. The simulated period lasts 5 mins for each phase. Every experiment is performed 10 times for each setting and the average measurements are reported. The randomly located nodes for the first evaluated system are recorded in order to use the exact same environment in all schemes.
The first case examines the normal operation of each scheme, with no attacks taking place. Fig. 4 depicts a snapshot from the simulation and its projection on Google maps. The different colors illustrate the maximum speed of the vehicles and the current average speed in each road segment. In general, as the processed data are spatial, the performance of MobileTrust can be affected by the density of the mobile nodes. Nevertheless, one of the main contributions of this paper is that the trust calculation can be distributed. Thus, if the same computational resources are devoted for every 13,000 citizens, the similar results will be concluded for medium-sized (50-100k residents) or even bigger (200-500k citizens) cities.
Then, malicious nodes are introduced. For each different attack, 5 experiments are performed for 10, 20, 30, 40, and 50 percentage of malicious nodes respectively (networks with higher volume of malicious entities are generally getting discarded in practice).
5.2 Normal Operation
In order to evaluate the trust systems under normal operation, we emulate around 100 traffic congestion events and 10 car crashes in each experiment. Two metrics estimate the performance and the energy consumption of each system. M₁-₁ measures the number of trust messages that are sent during normal operation, representing a rough estimation of the involving communication and computational overheads. M₁-₂ calculates the number of messages that are required in order to identify a road event, revealing the early notification capabilities of each scheme. For both metrics, the lower the value, the better. Fig. 5 illustrates the relevant metrics.
For M₁-₁, the MobileTrust authority receives one message by each involved vehicle. The rest P2P systems require a much higher number of messages in order to form the trust parameters, based on the information propagation scope. The SNTM’s closest node strategy has moderate performance while TBSE and VARS are less efficient. ERS requires the highest amount of interaction.
For M₁-₂, the MobileTrust publishes instantly a new road event when it is reported by a trusted or a legitimate user with high event reputation along with the current confidence level. Then, it takes a decent amount of incoming contributions in order to notify the event with high confidence. The rest systems take several messages until a node obtains sufficient knowledge regarding the event’s occurrence. Moreover, as direct interaction gains higher weight when integrating direct and indirect knowledge, the nodes in the P2P schemes usually have to detect the event by direct observation before being able to reason about it with high confidence. Among these systems, SNTM provides the earliest notification as indirect knowledge gives higher weight to the nodes that are closest to the event. TBSE, VARS, and ERS exhibit similar low performance.
As is evident by the two metrics, MobileTrust is the most efficient system with effective early notification of road events. Nonetheless, MobileTrust’s performance is normally even better as public authorities can report several types of scheduled events, helping the drivers to avoid the relevant segments without requiring any further contribution from them. The actual performance of MobileTrust is measured in a preliminary implementation on real devices and is detailed in the next Section.
5.3 Attack Scenarios
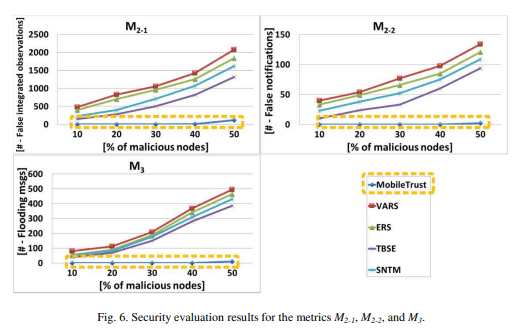
In the first attack, the malicious nodes launch a social-based on-off attack. They cooperate at the initialization phase to gain high trust values, while at the evaluation phase they start injecting false notifications. We evaluate the effectiveness of the knowledge integration mechanism of each system in detecting bogus data and producing accurate notifications regarding the road state by measuring the volume of the false observations that are integrated by the trust system, defined as M₂-₁, and the number of false notifications that are made by the system, defined as M₂-₂. For both metrics, the lower the value, the better. Fig. 6 illustrates the evaluation metrics M₂-₁ and M₂-₂.
For M₂-₁, the single and centralized authority of MobileTrust collects a high volume of legitimate votes and thus is able to recognize the malicious entities and reject their contributions. As the attackers increase, the system may integrate a small number of bogus observations at the beginning of the attack phase. Nevertheless, the authority can detect the misbehaving nodes fast, even for a high volume of attackers (50%). All relevant schemes perform poorly for a large number of attackers (>40%). TBSE rejects a high volume of bogus observations for a low and moderate percent of attackers (10%-30%) due to its enhanced trust evaluation process. SNTM, ERS, and VARS exhibit the worst results in all cases.
For M₂-₂, the central authority of MobileTrust reports only a small number of false notifications for a high volume of malicious nodes (50%). When many attackers participate in the attack (>40%) the relevant schemes perform badly, as they integrate a large number of bogus observations (M₂-₁). TBSE produces moderate results for low to moderate attackers’ volumes (10%-30%) as it processes less malicious messages. SNTM, ERS, and VARS have the lowest performance across all attack setups.
In the second scenario, the attackers exploit the ad hoc communication in order to perform rushing attacks by flooding messages and exhaust the resources of the other nodes. We estimate the robustness of the ad hoc communication against rushing attacks by calculating the number of flooding request messages that are processed by the legitimate nodes, defined as M₃, the lower the value the better. We consider that all messages contain valid data (not erroneous). Fig. 6also illustrates the metric M₃.
In MobileTrust, the nodes can instantly recognize the involved road segments from the notification format and ignore irrelevant requests. As the nodes exchange only public information, they can reason when a specific notification has been just sent and they will not retransmit it as long as they remain inside the same road segment. Moreover, each node imposes a maximum number of responses in the current time window. Thus, MobileTrust nodes will process a low volume of different requests, constraining the effectiveness and propagation of flooding. The P2P systems serve a high number of flooding requests under many colluding attackers. TBSE can degrade the flooding attack for a low to moderate volume of malicious participants (10%- 20%) as it detects selfish behavior and ranks negatively the relevant nodes. SNTM and ERS also provide adequate defense against a small amount of misbehaving nodes (10%). VARS offers little protection.
5.4 Security and Comparison with Other Systems
As is evident by the above analysis, MobileTrust implements efficient and robust mechanisms for knowledge integration and ad hoc communication that outperform the current state of the art. The proposed system offers immunity-by-design against some types of threats and attacks. It is not vulnerable to information cascading and oversampling as only first-hand observations are evaluated by a single centralized entity. Moreover, badmouthing and ballot-stuffing attacks are not applicable as no third-party recommendations about trust are supported. As nodes either advertise their observations directly to the authority or broadcast the public notifications to the other cars, the deletion of transmitted messages is not applicable, in contrast to the P2P trust schemes. Regarding privacy, P2P communication does not disclose any vehicle information, while restricted anonymous usage is supported for the centralized interaction. Eavesdropping is also ineffective as the transmitted messages are either encrypted communication between the authority and the vehicles or publicly available data.
The cryptographic solutions provide the mainstream security properties. Identity-based attacks (e.g. impersonation, newcomer, HELLO flooding, and Sybil attacks) are countered as the creator of each message is properly authenticated and evaluated. Session symmetric keys encrypt the transmitted data between the authority and the contributors, offering confidentiality and preventing information disclosure. The HMAC primitive enables integrity checks and detects message modification attempts. Random nonces are also included in the message data to avoid replay attacks. The system accomplishes non-repudiation regarding the actions of the authority and the knowledge contributors. Each entity performs a specific set of actions and role-based authorization is imposed for the central authority, the authenticated contributors, and the passive anonymous users.
Moreover, automatic access control techniques (i.e. the plaintext notification identifiers) and back-off mechanisms degrade the effectiveness of DoS attacks. The low computational/communicational overheads for each task and edge computing further enhances protection.
Table 2 summarizes the comparison results of MobileTrust and the 4 related schemes.
6 IMPLEMENTATION
This section presents the implementation details of MobileTrust on a smart city setting with a real vehicle. We evaluate the system’s performance under normal operation and measure the actual runtime overhead, which was sketched in the simulation study (subsection 5.2 Normal Operation).
6.1 The Car Installation
A real smart car setting is deployed by the authors in [39]. A smart phone, acting as the vehicle’s infotainment, collects information of the vehicles electronic control units (ECU) via a Bluetooth-enabled OBD scan tool, and communicates to Internet, via a Global System for Mobile Communications (GSM) connection, with a command-and control (C&C) center, located in the cloud. The research platform of GRNET Virtual MAchines (ViMA) is utilized for cloud computing. The VMs of the cloud service are monitored through a laptop. The emulated scenario implements the European Union’s road safety system eCall [40], where the system detects car accidents and automatically informs the involved emergency services. Fig. 7 depicts the smart car setting.
In this paper, we further extend this deployment in order to implement MobileTrust and model the event types that are described in Section 3. The in-vehicle component is an Android application, running in the smart phone, and the CA is implemented as a web service in the C&C.
6.2 Testbed
Under this setting, a testbed was evaluated on a VM (Intel Core i7 at 2.1 GHz CPU, 8GB RAM,64-bit OS Windows 8.1 Pro), where 1000 event notifications where advertised. Fig. 8 illustrates the response time of MobileTrust in ms for the smart phone client application and the central authority at the backend, with spikes depicting TLS processing. The additional communication delay through GSM was on average 1-4 seconds. The processing resource consumption of the internal components is summarized in Table 3. The V2V interactions also include the referred cryptographic services and exhibit similar results.
6.3 Parallelization in GPUs
As aforementioned, the core knowledge integration mechanism of MobileTrust can be parallelized in a fine-grained manner. Except from the CPU parallelization on multiple core, the GPUs is a well-tried practice that can drastically reduce the processing time in computation intensive operations. Recommendation systems perform well in this setting with 30-32 times speedup [38]. In this study, we utilize the CUDA General Purpose GPU (GPGPU) in order to parallelize the MobileTrust algorithm. The GPU-accelerated deployment is implemented on the same machine as the CPU version, equipped with the NVIDIA GeForce GTX 1050 GPU (640 cores, 2GB buffer, 6Gbps memory speed, 1.4 GHz clock).
Consider the most frequent and resource demanding traffic congestion events for road segments with 500 vehicles on average. After the event’s active period, the event’s confidence must be evaluated (see Table 3). Then, the reputation histories and the trust structures of the 500 users must be updated. Fig. 9 depicts the average processing time of evaluating a road event for the CPU, CPU-accelerated, and GPU-accelerated versions of MobileTrust. With the parallel processing on 4 CPU cores (8 threads), each thread processes one event for a specific road segment and updates the users’ data. The CPU parallelism busts performance by 23% in comparison with the single CPU version. This CPU-accelerated implementation is further improved by parallelizing the users’ data update in the GPU (500 cores of 560KB each). This setting is around 32 times faster than the single CPU one, and can serve 1.16 events per second. The optimized proposal can be deployed by every VM in both cloud and MEC architectures, providing an overall efficient and globally scalable system with real-time response.
4 CONCLUSIONS
In this work MobileTrust – a trust-based resource sharing system for VANETs is presented. The system is modelled in the SUMO simulator along with 4 relevant schemes and a comparative analysis is conducted. MobileTrust is an energy efficient solution that provides the higher level of protection. On real embedded devices in the context of an emulated VANET and smart city CPS, the overhead of the trust scheme is low and acceptable for the added security and the overall protection level that it is achieved.
One limitation for MobileTrust and all the relevant systems concerns the accuracy of the location positioning system [41]. For example, the discrimination of the different lanes in a road section may not be possible. Thus, if only one lane faces a specific event (i.e. traffic jam), the notification and rating mechanisms can produce erroneous results. Nevertheless, these issues will be contained as the Global Positioning System (GPS) technology is evolved and integrated with 5G pioneering frequency communications (such as 26 and 60GHz).
As future extensions of our work, we consider the further inclusion of modern smart transportation technologies and circular economy business models. The goal is to extend the trust mechanism in order to evaluate application specific features for ecosystems that provide operations like ride service hailing and car-sharing.
ACKNOWLEDGMENTS
This work has received funding from the European Union Horizon’s 2020 research and innovation programme H2020-DS-SC7-2017, under grant agreements No. 786890 (THREATARREST) and No. 830927 (CONCORDIA), as well as the Marie Skodowska-Curie Actions (MSCA) Research and Innovation Staff Exchange (RISE), H2020-MSCA-RISE-2017, under grant agreements No. 777855 (CE-IoT) and No. 778228 (Ideal-Cities).
REFERENCES
[1] N. Trent, “Cyber physical system 2017 market segmentation, application, technology & market analysis research report to 2021,” Wiseguyreports.com, Maharashtra, India, October 2017, [On-line] https://www.abnewswire.com/pressreleases/cyber-physical-system-2017-marketsegmentationapplicationtechnology-market-analysis-research-report-to2021_150981.html .
[2] A. Dahiya and R. K. Chauhan, “A comparative study of MANET and VANET environment,” Journal of Computing, SCRIBD, vol. 2, issue 7, pp. 87-92, July 2010.
[3] F. J. Martinez, C. K. Toh, J.-C. Cano, C. T. Calafate, and P. Manzoni, “A survey and comparative study of simulators for vehicular ad hoc networks (VANETs),” Wireless Communications & Mobile Computing, Wiley, vol. 11, issue 7, pp. 813-828, July 2011.
[4] P. Chouhan, G. Kaushal, and U. Prajapath, “Comparative study MANET and VANET,” International Journal of Engineering and Computer Science, vol. 5, issue 04, pp. 16079-16083, April 2016.
[5] N. Saxena, S. Grijalva, V. Chukwuka, and A. V. Vasilakos, “Network security and privacy challenges in smart vehicle-to-grid,” IEEE Wireless Communications, IEEE, vol. 24, issue 4, pp. 88-98, August 2017.
[6] C. K. Toh, “Future application scenarios for MANET-based intelligent transportation systems,” Future Generation Communication and Networking (FGCN), IEEE, Jeju, South Korea, pp. 1-4, January 2008.
[7] F. J. Martinez, C. K. Toh, J.-C. Cano, C. T. Calafate, and P. Manzoni, “Emergency services in future intelligent transportation systems based on vehicular communication networks,” IEEE Intelligent Transportation Systems Magazine, IEEE, vol. 2, issue 2, pp. 6-20, Summer 2010.
[8] B. Cici, A. Markopoulou, and N. Laoutaris, “SORS: a scalable online ridesharing system,” 9thInternational Workshop on Computational Transportation Science (IWCTS), ACM SIGSPATIAL, Burlingame, California, pp. 13-18, October 2016.
[9] S. Grafling, P. Mahonen, and J. Riihijarvi, “Performance evaluation of IEEE 1609 WAVE and IEEE 802.11p for vehicular communications,” 2ndInternational Conference on Ubiquitous and Future Networks (ICUFN), IEEE, Jeju Island, South Korea, pp. 344-348, August 2010.
[10] Y. Wang, A. Ahmed, B. Krishnamachari, and K. Psounis, “IEEE 802.11p performance evaluation and protocol enhancement,” IEEE International Conference on Vehicular Electronics and Safety (ICVES), IEEE, Columbus, OH, USA, pp. 317- 322, September 2008.
[11] D. Eckhoff, N. Sofra, and R. German, “A performance study if cooperative awareness in ETSI ITS G5 and IEEE WAVE,” 10thAnnual Conference on Wireless On-demand Network Systems and Services (WONS), IEEE, Banff, AB, Canada, pp. 196-200, August 2013.
[12] X. Gong and N. B. Shroff, “Trustful mobile crowdsensing for strategic users with private qualities,” 15 thInternational Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks (WiOpt), IEEE, Paris, France, May 2017.
[13] M. Mejia and R. haparro-Vargas, “Distributed trust and reputation mechanisms for vehicular ad-hoc networks,” Vehicular Technologies – Deployment and Applications, INTECH, Chapter 6, pp. 117-140, 2013.
[14] N. J. Patel and R. H. Jhaveri, “Trust based approaches for secure routing in VANET: a survey,” International Conference on Advanced Computing Technologies and Applications (ICACTA), Elsevier, Procedia Computer Science, vol. 45, pp. 592- 601, March 2015.
[15] M. A. Ngadi, R. H. Khokhar, and S. Mandala, “A review of current routing attacks in mobile ad-hoc networks,” International Journal of Computer Science and Security, vol. 2, issue 3, pp. 18-29, 2008.
[16] D. Airehrour, J. Gutierrez, and S. K. Ray, “Secure routing for Internet of things,” Journal of Network and Computer Applications, Elsevier, vol. 66, pp.198-213, May 2016.
[17] E. Carrara and G. Hogden, “ENISA: reputation-based system: a security analysis,” European Network and Information Security Agency (ENISA) Position Papre, no. 2, October 2007.
[18] J. Zhang, “Trust management for VANETs: challenges, desired properties and future directions,” International Journal of Distributed Systems and Technologies, vol. 1, issue 1, pp. 48-62, January-March 2012.
[19] S. A. Soleymani, A. H. Abdullah, W. H. Hassan, M. H. Anisi, S. Goudarzi, M.A. R. Baee, and S. Mandala, “Trust management in vehicular ad hoc network: a systematic review,” EURASIP Journal on Wireless Communications and Networking, Springer, vol. 2015, article 146, pp. 1-22, December 2015.
[20] F. Dotzer, L. Fischer, and P. Magiera, “VARS: a Vehicle Ad-hoc network Reputation System,” 6thIEEE International Symposium on a World of Wireless Mobile and Multimedia Networks (WoWMoM), IEEE, Taormina-Giardini Naxos, Italy, pp. 454-456, June 2005.
[21] N.-W. Lo and H.-C. Tsai, “A reputation system for traffic safety event on vehicular ad hoc networks,” EURASIP Journal on Wireless Communications and Networking – Special Issue on enabling Wireless Technologies for Green Pervasive Computing, Springer, vol. 2009, no. 9, article ID 125348, pp. 1-10, February 2009.
[22] Z. Wei, F. R. Yu, and A. Boukerche, “Trust based security enhancements for vehicular ad hoc networks,” 4thACM International Symposium on Development and Analysis of Intelligent Vehicular Networks and Applications (DIVANet), ACM, Montreal, QC, Canada, pp. 103-109, September 2014.
[23] G. Shafer and J. Pearl, “Readings in Uncertain Reasoning,” Morgan Kaufman Publishers, pp. 1-768, July 1990.
[24] Z. Huang, S. Ruj, M. A. Cavenaghu, M. Stojmenovic, and A. Nayak, “A social network approach to trust management,” Peer-to-Peer Networking and Applications, Springer, vol.7, issue 3, pp. 229-242, September 2014.
[25] Q. Kong, R. Lu, M. Ma, and H. Bao, “A privacy-preserving sensory data sharing scheme in Internet of Vehicles,” Future Generation Computer Systems, Elsevier, vol. 92, pp. 644-655, March 2019.
[26] A. Machen, S. Wang, K. K. Leung, B. J. Ko, and T. Salonidis, “Migrating running applications across mobile edge clouds: poster,” 22ndAnnual International Conference on Mobile Computing and Networking (MobiCom), ACM, New York, USA, pp. 435-436, October 2016.
[27] L. Gkatzikis and I. Koutsopoulos, “Mobiles on cloud nine: efficient task migration policies for cloud computing systems,” 3rd International Conference on Cloud Networking (CloudNet), IEEE, Luxembourg, pp. 204-210, October 2014.
[28] S. Ioannidis and P. Marbach, “On the design of hybrid peer-to-peer systems,” International Conference on Measurements and Modeling of Computer Systems (SIGMETRICS), ACM, Annapolis, MD, USA, pp. 157-168, June 2008.
[29] Y. Zhang, L. Xu, and X. Wang, “A cooperative secure routing protocol based on reputation system for ad hoc networks,” Journal of Communications, vol. 3, no. 6, pp. 43-50, November 2008.
[30] M. Armbrust, A. Fox, R. Griffith, A. D. Joseph, R. Katz, A. Konwinski, G. Lee, D. Patterson, A. Rabkin, I. Stoica, and M. Zaharia, “A view of cloud computing,” Communications of the ACM, ACM, vol. 53, no. 4, pp. 50-58, April 2010.
[31] W. Tian, Y. Zhao, Y. Zhong, M. Xu, and C. Jing, “A dynamic and integrated load-balancing scheduling algorithm for Cloud datacenters,” IEEE International Conference on Cloud Computing and Intelligence Systems (CCIS), IEEE, Beijing, China, pp. 311-315, September 2011.
[32] J. Kubiatowicz, D. Bindel, Y. Chen, S. Czerwinski, P. Eaton, D. Geels, R. Gummadi, S. Rhea, H. Weatherspoon, W. Weimer, C. Wells, and B. Zhao, “OceanStore: An Architecture for Global-Scale Persistent Storage,” ACM SIGPLAN Notices, ACM, vol. 35, issue 11, pp. 190-201, November 2000.
[33] B. Blanchet, “Automatic verification of security protocols in the symbolic model: the verifier ProVerif,” Foundations of Security Analysis and Design (FOSAD) VII, Springer, LNCS, vol. 8604, pp. 54-87, 2014.
[34] I. Ristic, “OpenSSL cookbook,” Feisty Duck, pp. 1-94, March 2016.
[35] S. Yang, S. Ji, and R. Beyah, “DPPG: A Dynamic Password Policy Generation System,” IEEE Transactions on Information Forensics and Security, IEEE, vol. 13, no. 3, pp. 545-558, March 2018.
[36] Y. S. Han, H.-T. Pai, R. Zheng, and W. H. Mow, “Efficient exact regenerating codes for Byzantine fault tolerance in distributed networked storage,” IEEE Transactions on Communications, IEEE, vol. 62, issue 2, pp. 385-397, February 2014.
[37] G. Hatzivasilis, I. Papaefstathiou, and C. Manifavas, “ModConTR: a Modular and Configurable Trust and Reputationbased system for secure routing in ad-hoc networks,” 11th ACS/IEEE International Conference on Computer Systems and Applications (AICCSA), IEEE, Doha, Qatar, November 2014.
[38] A. V. Rodrigues, A. Jorge, and I. Dutra, “Accelerating recommender systems using GPUs,” 30th Annual ACM Symposium on Applied Computing (SAC), ACM, Salamanca, Spain, pp. 879-884, April 2015.
[39] K. Fysarakis, G. Hatzivasilis, I. Papaefstathiou, and C. Manifavas, “RtVMF: A secure real-time vehicle management framework with critical incident response,” IEEE Pervasive Computing Magazine (PVC), Special Issue on Smart Vehicle Spaces, IEEE, vol. 15, issue 1, pp. 22-30, January 2016.
[40] J. Hayes, “Calling all cars,” IET Engineering & Technology, IET, vol. 9, issue 3, pp. 58-61, April 2014.
[41] Q. Pei, B. Kang, L. Zhang, K.-K. R. Choo, Y. Zhang, and Y. Sun, “Secure and privacy-preserving 3D vehicle positioning schemes for vehicular ad hoc network,” EURASIP Journal on Wireless Communications and Networking, Springer, vol. 2018, issue 1, article 271, pp. 1-12, December 2018.


























































































































0 Comments